
The first step in solving a problem is to recognize that it does exist. Zig Ziglar
It is important for us to know what the weaknesses in computer systems in order to know how to secure them. To that end MITRE maintains lists of computer vulnerabilities and weaknesses in software systems. They recently updated the list of weaknesses the Common Weakness Enumeration. It is a community-developed list that helps cybersecurity professionals identify weaknesses so they can be addressed. From the site:
"CWE™ is a community-developed list of common software security weaknesses. It serves as a common language, a measuring stick for software security tools, and as a baseline for weakness identification, mitigation, and prevention efforts."
One major benefit of the list is the "common language" allowing practitioners to discuss the issues in a standard way.
The list of top 25 lists was recently updated. Updates to the list may reflect new weaknesses, new mitigations, or more information about weaknesses. Sadly, there has been little change in the top of the top 25 list. Improper Input Validation, SQL Injection, and Information Exposure are still on the list. These and many others from the top of the list are discussed in Learning Tree's Introduction to Cybersecurity and Introduction to Cybersecurity - a Starter Guide.
The list not only describes the issues in detail but often includes programming examples illustrating the weaknesses as well as instructions on how to avoid those weaknesses in software design and coding.
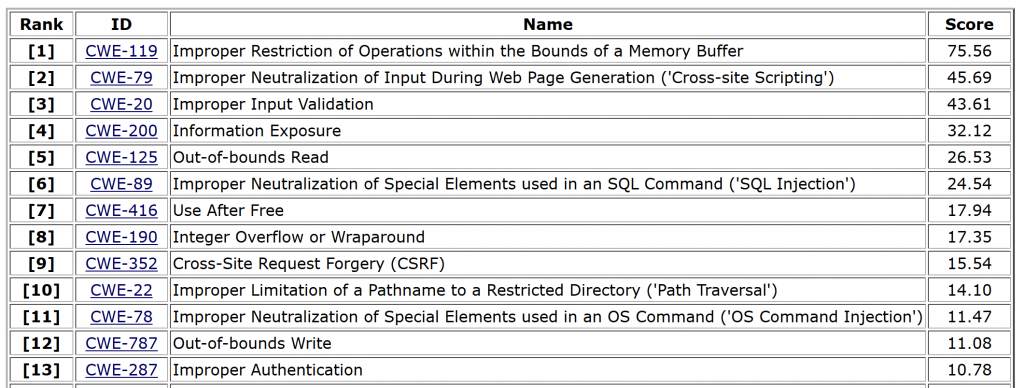
From https://cwe.mitre.org/top25/archive/2019/2019_cwe_top25.html
Let's look at three weaknesses:
- Improper Input Validation. The CWE defines this as: "The product does not validate or incorrectly validates input that can affect the control flow or data flow of a program." When I mention this to course participants, the example I give is, "What happens when a program expects a number between 10 and 20 and the user types '99'?"
Every program, from web back ends to smartphone apps to full-blown applications needs to validate the user input and act accordingly (ask again for a value, display an error, or whatever). - SQL Injection or more formally, 'Improper Neutralization of Special Elements used in an SQL Command'. SQL is a database programming language, user input is often used in database searches, for example as a name for which to search in a database. As with Improper Input Validation (of which this is a specific case), programmers need to ensure the data is valid: a user should not be able to enter a database command at an input prompt or in a dialog box. Doing so could damage the database or expose sensitive information.
- Information Exposure. This is exactly what it sounds like: software that unintentionally displays potentially sensitive information to a user. Reports of breaches where user names, passwords, email, or credit card information are common. The cause may be SQL Injection or another weakness leading to a vulnerability that is exploited.
Many of these weaknesses are simple oversight: a programmer checks a number against a maximum, but not a minimum, for instance. The biggest problem is that programmers are taught - not explicitly, of course - that a program is good if it "works" for specified input. Few are taught to program defensively: for example, to check every input, array reference, and system call to ensure that the result is within the bounds of expectations.
The CWE list should help programmers and developers identify potential weakness in their code, and importantly it should help educators make students aware of how to program defensively.
To your safe computing,


